Title: Authentication and authorization · Issue #504 · feast-dev/feast · GitHub
Open Graph Title: Authentication and authorization · Issue #504 · feast-dev/feast
X Title: Authentication and authorization · Issue #504 · feast-dev/feast
Description: Creating this issue to track the discussion around user authentication & authorization. 1. Prior Art: Auth as proposed in the Feast Projects RFC In the Feast: Projects RFC we proposed a basic form of authentication as a "minmal" implemen...
Open Graph Description: Creating this issue to track the discussion around user authentication & authorization. 1. Prior Art: Auth as proposed in the Feast Projects RFC In the Feast: Projects RFC we proposed a basic form ...
X Description: Creating this issue to track the discussion around user authentication & authorization. 1. Prior Art: Auth as proposed in the Feast Projects RFC In the Feast: Projects RFC we proposed a basic f...
Opengraph URL: https://github.com/feast-dev/feast/issues/504
X: @github
Domain: github.com
{"@context":"https://schema.org","@type":"DiscussionForumPosting","headline":"Authentication and authorization","articleBody":"Creating this issue to track the discussion around user authentication \u0026 authorization. \r\n\r\n### 1. Prior Art: Auth as proposed in the Feast Projects RFC\r\nIn the [Feast: Projects RFC](https://docs.google.com/document/d/14-QBz9X8zK_aGAY2ti43a7PqMxvqp0035ec7QYgmEBM/edit#heading=h.c29o6bkcurw9) we proposed a basic form of authentication as a \"minmal\" implementation for Feast 0.5.\r\n\r\n**Overview**\r\nAt a high level, this proposal adds user authentication based on a new user table that Feast maintains. No API is made available to manage the creation/removal of users, but the actions taken by users is on the Feast Core API is limited to the resources they have access to. Resource access is managed only based on membership of users to projects. \r\n\r\nNote on Roles: \"Roles\" were originally proposed but will be delayed until a future release can implement them properly. Right now there is only a full \"owner\" role which is implicit. All users either have ownership of a project, or not.\r\n\r\n**Assumptions**:\r\n- User authentication only applies to Feast Core, not ingestion or \"serving\".\r\n\r\n**Out of scope**:\r\n- Full user management (create or remove users, or manage user profiles).\r\n- JWT or functionality like sessions on user auth.\r\n- RBAC\r\n\r\n**Data model**\r\n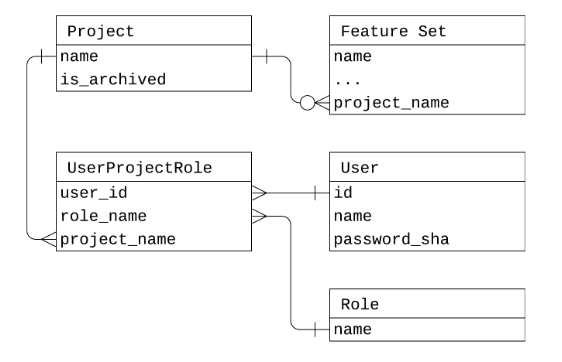\r\n\r\n**API**\r\n- Feast Core API\r\n - New RPCs\r\n - AddMember: Add a user to a specific project\r\n - RemoveMember: Remove user from a specific project\r\n - ListMembers: List members in a project\r\n - ~~AddRole~~\r\n - ~~RemoveRole~~\r\n- Feast Core Data Model\r\n - New table\r\n - Users: Users table\r\n - UserProjects: Relation between users \u0026 projects\r\n - ~~Roles: Roles table~~\r\n - ~~UserProjectRole: Relation between roles, users, and projects~~\r\n - New classes\r\n - Users\r\n - ~~Roles~~\r\n- Python SDK\r\n - Addition of user auth configuration\r\n - New methods:\r\n - add_member()\r\n - remove_member()\r\n - list_members()\r\n - ~~add_role()~~\r\n - ~~remove_role()~~\r\n\r\n### 2. Objectives\r\nThe main objective of this issue is to finalize two proposals. The first is a \"minimal\" set of functionality that we want to support, and the second is a \"full\" set of functionality. Since Feast 0.5 is our next release, the priority is to finalize the implementation of the minimal release.\r\n\r\n* **Minimal**: To implement a basic form of authentication in Feast 0.5. \r\n* **Full**: Create an extensible/pluggable authentication \u0026 authorization system that supports multiple providers, can be used by both services and users, and covers ingestion, Core, and serving. No PR exists for this functionality yet.\r\n\r\n### 3. Requirements (minimal release)\r\nThe following user stories should be supported as part of the first minimal release (Feast 0.5).\r\n\r\n#### 3.1 User stories\r\n1. As a Feast user, so that I can prevent other users from modifying my feature sets, I would like to have a way to prevent modification of feature sets by unauthorized users.\r\n2. ~~As a Feast user, so that I can prevent other users from seeing my feature sets, I would like to have a way to limit access to certain users to view my feature sets~~ [Edit: Removing this story. It would be simpler to allow full view access]\r\n3. As a Feast user, so that I can allow my team to modify/view my feature sets, I would like to have a way to selectively grant or revoke access to feature sets for specific users.\r\n4. As a Feast user, so that I can grant access to multiple feature sets in a project, I would like to manage access control to feature sets at the project level\r\n5. As a Feast user, so that Feast can uniquely identify me, I would like to be able to authenticate myself to Feast.\r\n\r\n#### 3.2 In Scope\r\n- Authentication of users\r\n- Management of membership of users to projects for the purposes of granting access to feature sets within those projects\r\n- Project level access control (read vs write) based on membership of projects\r\n\r\n#### 3.3 Out of Scope\r\n- Full authorization or RBAC.\r\n- Stream, ingestion, and serving are also out of scope for the purposes of authentication and authorization.\r\n- Full user management (create or remove users, or manage user profiles).\r\n- JWT or functionality like sessions on user auth.\r\n\r\n### 4. Open questions\r\n- Which authentication frameworks or providers should be supported for Feast 0.5?\r\n- Are there any frameworks or open source services that would make implementing authorization safer, especially offload the responsibility of managing user credentials?\r\n- Do our long term and short term goals for both user authentication and authorization align?\r\n- What should be in scope for authentication for Feast 0.5?\r\n","author":{"url":"https://github.com/woop","@type":"Person","name":"woop"},"datePublished":"2020-02-29T06:14:01.000Z","interactionStatistic":{"@type":"InteractionCounter","interactionType":"https://schema.org/CommentAction","userInteractionCount":21},"url":"https://github.com/504/feast/issues/504"}| route-pattern | /_view_fragments/issues/show/:user_id/:repository/:id/issue_layout(.:format) |
| route-controller | voltron_issues_fragments |
| route-action | issue_layout |
| fetch-nonce | v2:925117bd-333a-d74a-fe68-b3f2de93a033 |
| current-catalog-service-hash | 81bb79d38c15960b92d99bca9288a9108c7a47b18f2423d0f6438c5b7bcd2114 |
| request-id | C56E:261BF9:8AF75D:C2D210:6979C4FE |
| html-safe-nonce | 860a8e4c4cd132cd53590ee391d140600a177f7ee685ed6c0c79e01c6bcafe05 |
| visitor-payload | eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDNTZFOjI2MUJGOTo4QUY3NUQ6QzJEMjEwOjY5NzlDNEZFIiwidmlzaXRvcl9pZCI6IjkwMDYxMzY1Njg2Nzg4MjIzOCIsInJlZ2lvbl9lZGdlIjoiaWFkIiwicmVnaW9uX3JlbmRlciI6ImlhZCJ9 |
| visitor-hmac | 0856d8f787e11e24edad356e31733670712d7669775c7dfad730dcbe7901f34c |
| hovercard-subject-tag | issue:573204254 |
| github-keyboard-shortcuts | repository,issues,copilot |
| google-site-verification | Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I |
| octolytics-url | https://collector.github.com/github/collect |
| analytics-location | / |
| fb:app_id | 1401488693436528 |
| apple-itunes-app | app-id=1477376905, app-argument=https://github.com/_view_fragments/issues/show/feast-dev/feast/504/issue_layout |
| twitter:image | https://opengraph.githubassets.com/cc2e4bd4f1d266c6ee0557c000d2efa34ee1bfd9439209f2a73420022f7afaea/feast-dev/feast/issues/504 |
| twitter:card | summary_large_image |
| og:image | https://opengraph.githubassets.com/cc2e4bd4f1d266c6ee0557c000d2efa34ee1bfd9439209f2a73420022f7afaea/feast-dev/feast/issues/504 |
| og:image:alt | Creating this issue to track the discussion around user authentication & authorization. 1. Prior Art: Auth as proposed in the Feast Projects RFC In the Feast: Projects RFC we proposed a basic form ... |
| og:image:width | 1200 |
| og:image:height | 600 |
| og:site_name | GitHub |
| og:type | object |
| og:author:username | woop |
| hostname | github.com |
| expected-hostname | github.com |
| None | c049b65ec7e54cbf2521f5a560b6527714c612b0bd169188e2ea6e16f83bd5f4 |
| turbo-cache-control | no-preview |
| go-import | github.com/feast-dev/feast git https://github.com/feast-dev/feast.git |
| octolytics-dimension-user_id | 57027613 |
| octolytics-dimension-user_login | feast-dev |
| octolytics-dimension-repository_id | 161133770 |
| octolytics-dimension-repository_nwo | feast-dev/feast |
| octolytics-dimension-repository_public | true |
| octolytics-dimension-repository_is_fork | false |
| octolytics-dimension-repository_network_root_id | 161133770 |
| octolytics-dimension-repository_network_root_nwo | feast-dev/feast |
| turbo-body-classes | logged-out env-production page-responsive |
| disable-turbo | false |
| browser-stats-url | https://api.github.com/_private/browser/stats |
| browser-errors-url | https://api.github.com/_private/browser/errors |
| release | 87b137883e35e2766c3d0f6a257c4044f6390b83 |
| ui-target | full |
| theme-color | #1e2327 |
| color-scheme | light dark |
Links:
Viewport: width=device-width